The T-Systems GCP Sovereign Cloud is a cloud offering designed to deliver cloud services while simultaneously addressing stringent data sovereignty, compliance, and security requirements, primarily for organizations operating in regulated industries or in regions with strict data protection laws, such as the European Union (EU). This solution is a collaboration between T-Systems, a subsidiary of Deutsche Telekom, and Google Cloud Platform (GCP), leveraging Google Cloud’s technologies with T-Systems’ expertise in meeting local compliance and regulatory demands.
How the T-Systems GCP Sovereign Cloud works
With the T-Systems Sovereign Cloud powered by Google Cloud, GCP is transferring responsibility for sovereignty controls to T-Systems. The soverignty controls monitored and controlled by T-Systems are laid out in the diagram below.

T-Systems is monitoring the platform from outside in their own T-Systems Security Operations Center (SOC).
In the future, T-Systems and Google are planning to introduce two additional variants of the sovereign Google Cloud: The Supervised Cloud by T-Systems and the Hosted Cloud by T-Systems. The supervised cloud will be based on Google Supervised Cloud and the hosted cloud will be based on Google Distributed Cloud.
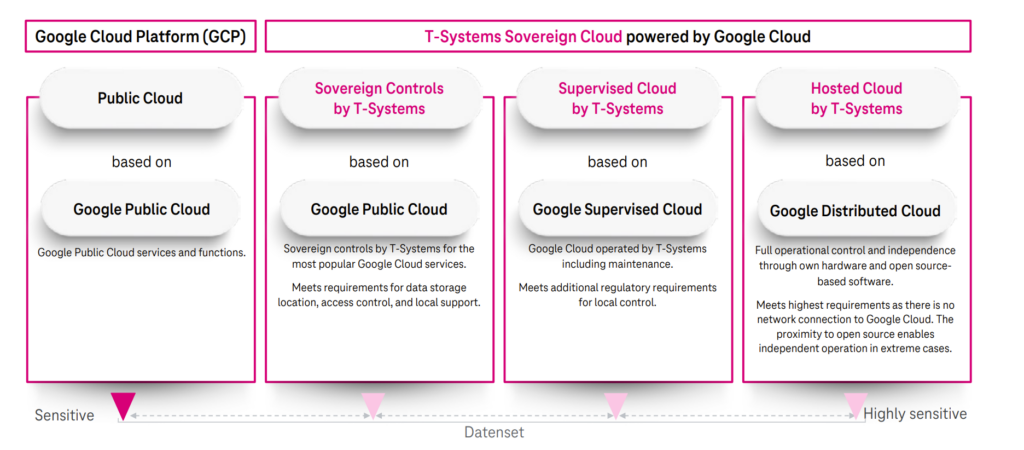
The Supervised Cloud by T-Systems is essentially a “semi-connected” variant of GCP, which is operated separately from other Google Cloud infrastructure by T-Systems.
The Hosted Cloud by T-Systems is a fully independent instance of GCP, fully air gapped, with it’s own IAM and no connection to global GCP. It is also operated by T-Systems but can be hosted in the customer’s data centre, if desired. This is similar to the model Oracle is offering with the sovereign variants of Oracle Cloud Infrastructure.
Available Services
The T-Systems Sovereign Cloud, powered by Google Cloud, essentially operates as the standard Google Cloud Platform (GCP), with T-Systems overseeing and managing the sovereignty controls. While all GCP services are technically accessible, not all are fully supported by the sovereignty control mechanisms. A list of services that are supported and managed under T-Systems’ sovereignty framework is:
- Artifact Registry
- BigQuery
- Cloud Bigtable
- Cloud Composer
- Cloud DNS
- Cloud External Key Manager (Cloud EKM)
- Cloud Key Management Service
- Cloud HSM
- Cloud Interconnect
- Cloud Load Balancing
- Cloud Logging
- Cloud NAT (Network Address Translation)
- Cloud Router
- Cloud Spanner
- Cloud SQL
- Cloud Storage
- Cloud VPN
- Compute Engine
- Dataflow
- Dataproc
- Google Cloud Identity-Aware Proxy
- Google Kubernetes Engine
- Identity & Access Management (IAM)
- Network Connectivity Center
- Persistent Disk
- Pub/Sub
- Service Directory
- Virtual Private Cloud
- VPC Service Controls
Source: Scope of Sovereign Controls by Partners Solutions.
Sovereign GCP Regions
The Sovereign Controls are implemented on a service level, rather than on a region level. Therefore, all GCP regions can be used with T-Systems controlling and supervising sovereignty.
The Supervised Cloud by T-Systems is going to be hosted by T-Systems. Here, the question about data centres becomes relevant. Details about that variant have yet to be announced. However, it is fair to assume that it is going to be hosted in the same regions as Open Telekom Cloud, namely all or one of the twin-core regions
- Biere and Magdeburg in Germany
- Almere and Aalsmeer in the Netherlands
- Zollikofen and Bern in Switzerland
Check the Data Centre map to see where these are geographically.
Conclusion
The approach of Google is similar to the Microsoft Cloud for Sovereignty in the sense that sovereignty controls are built into the platform. The difference is that supervision of these controls is outsourced to T-Systems. With the announced variants of sovereign GCP, T-Systems and Google will be offering a range of options for sovereign GCP. It remains to be seen how successful those models are going to be and if the right lessons were learned from the failure of the Microsoft Cloud Germany, operated by T-Systems.

